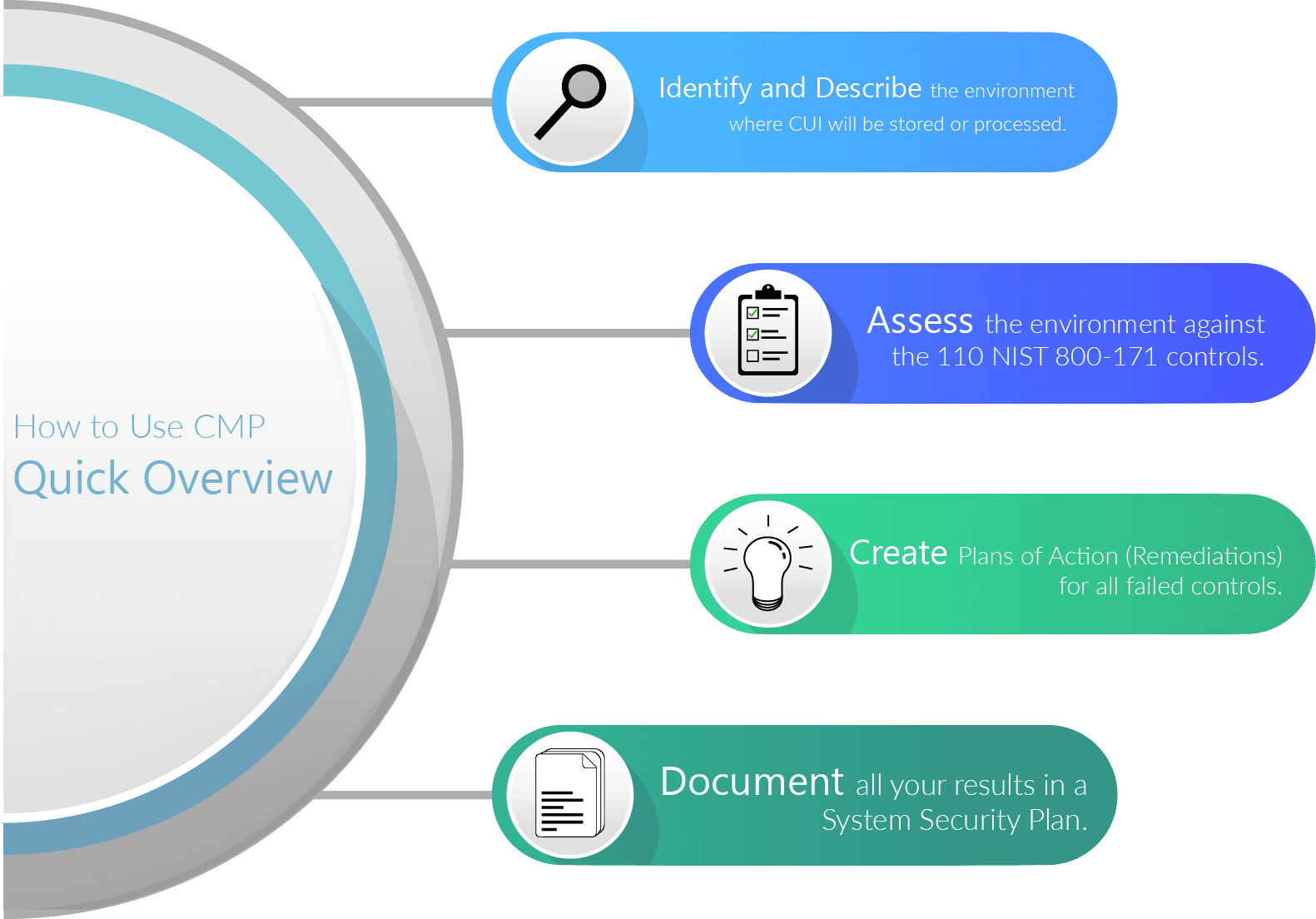
There is only one reason to use CMP: to prove you’re compliant with NIST 800-171. At a high-level, these are the steps you’ll need to take.

-
- Identify and describe the environment where CUI will be stored or processed.
- Organization Name
- Environment Name
- Environment Description
- Environment Contacts
- Operational Status
- System Boundary
- Interconnections
- Identify and describe the environment where CUI will be stored or processed.

- Assess the environment against the 110 NIST 800-171 controls.
- Understand the control requirements, and determine if the environment satisfies the requirements.
- Assign a control status for each control: Implemented, Not Implemented, Not Applicable, In Progress, or Not Started.
- Implemented (Previously “Passed”) – The requirements are clearly satisfied in your environment.
- Not Implemented (Previously “Failed”)- Your environment is unable to meet some part of the requirements.
- Not Applicable – The control clearly does not apply to your environment (e.g. a wireless network control does not apply to your environment if you do not use wireless networking).
- In Progress – An assessment of the current requirement has been started but has yet to be finished.
- Not Started – An assessment of the current requirement has not yet been started.
- Document your rationale for assigning a status for each control. If your environment passes a control, describe precisely why. If a control is not applicable, explain in detail and leave no room for questions.
- Upload evidence for all non-failed controls. This evidence might be a screenshot of a technical configuration proving you pass a control. It may be an organizational policy document or a photo of a locked server cabinet. Make sure the evidence supports the claims you’ve made.

- Create Plans of Action (Remediations) for all failed controls.
- You can still maintain NIST 800-171 compliance with failed controls, as long as you’ve documented your intentions to correct any deficiencies.
- Describe the deficiency and the action you will take to comply with the failed control.

- Document all your results in a System Security Plan.
- Attest to the accuracy of the assessment by certifying the results.
- Generate a new System Security Plan at the completion of the assessment and anytime changes are made.




